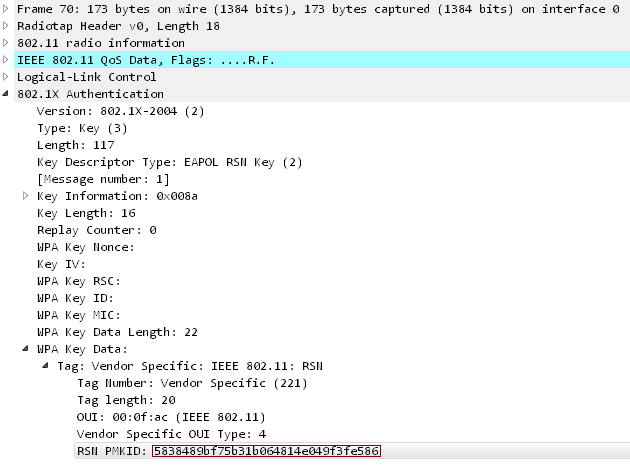
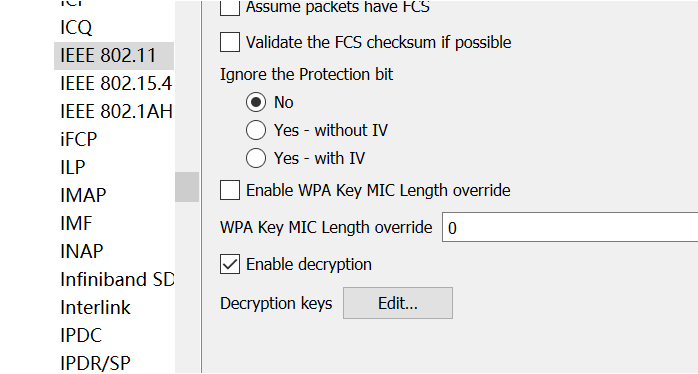
GitHub - n0mi1k/pmkidcracker: A tool to crack WPA2 passphrase with PMKID value without clients or de-authentication
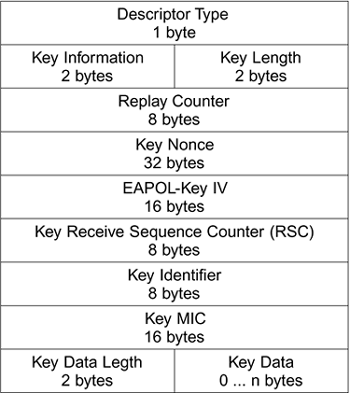
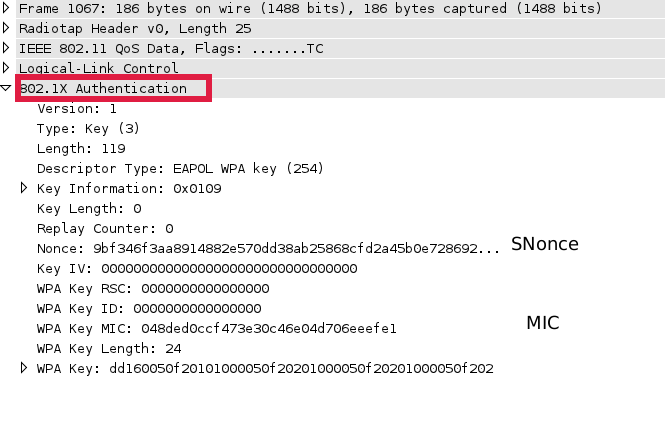
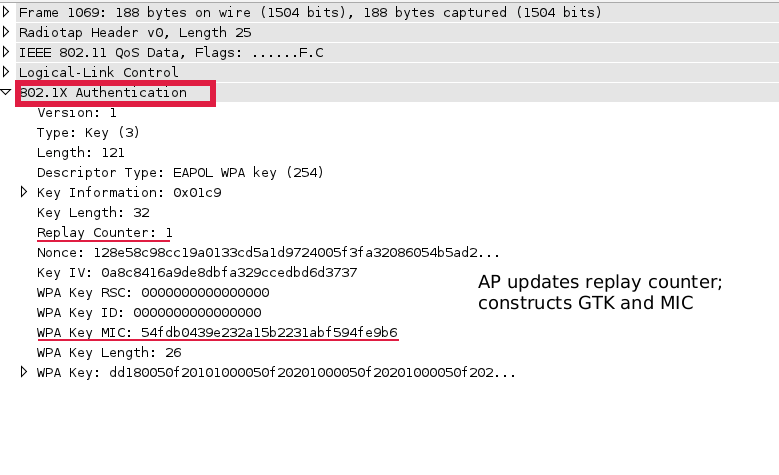
Details of Key Derivation for WPA :: Chapter 10. WPA and RSN Key Hierarchy :: Part II: The Design of Wi-Fi Security :: 802.11 security. wi-fi protected access and 802.11i :: Networking :: eTutorials.org

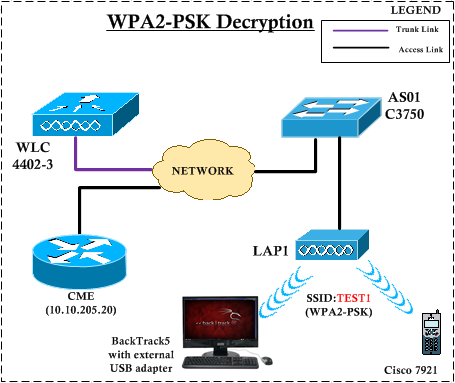
WPA-2 encryption and integrity check Message integrity check (MIC): AES... | Download Scientific Diagram